Vikram Chandrasekaran
Chief Technology Officer

Tuan Ousman
DevOps and IDM Engineer

Ganesh Srinivasan
DevOps and IDM Engineer
The rapid adoption of Cloud Computing, Containerization and DevOps practices in recent times has enabled organizations to move web-based software to end-users with increased velocity and frequency. In this blog post, we discuss some benefits of using a cloud-first approach, and how Like Minds can help organizations successfully adopt a cloud-first strategy. As an example, we discuss how to use Azure Managed Kubernetes Service (AKS) to implement a multi-region PingDirectory cluster using Ping Identity’s official repositories.
Evolution of Identity and Access Management (IAM) deployment to Cloud-First Strategy
In recent times, the rapid adoption of Cloud Computing, Containerization, and DevOps practices has enabled organizations to move web-based software to end-users with increased velocity and frequency. With the ever-changing business landscape and customer needs, the cloud-first approach has become the way forward to stay agile and competitive.
In the context of Identity and Access Management (IAM), we start seeing a paradigm shift in how IAM solutions are deployed and managed. Traditional deployments of IAM solutions on On-Premise infrastructure, which are fully maintained and operated by an organization, are now gradually being shifted to Managed Cloud Services like Azure AKS, Amazon EKS, Google GKE, etc. This reduces administrative overhead significantly by abstracting operational complexity.
Some of the benefits that organizations experience as they adopt to Cloud and Automation processes are:*
- High availability
- Zero-downtime updates
- Portability
- Scalability
- Reduced cost and risk
- Faster automated testing and feature updates
DevOps@LikeMinds and Kubernetes
With over two decades of experience as a Managed Security Service provider (MSSP), Like Minds is a trusted leader in providing organizations with cloud based IAM solutions. With our wealth of knowledge in Cloud Computing and Security, Like Minds is ideally positioned to synergize all Ping Identity products and DevOps practices. We remain strongly committed to cloud automation through containerization. Organizations can now benefit from containerization by leveraging Ping Identity products using Kubernetes. Tools such as Ping Identity’s Docker Images, Ping Identity Helm Charts, and Server Profiles are available to automate the deployment and management of containerized Ping Identity products. Learn more about Kubernetes. In this blog, we will provide a high-level overview of how to use Azure’s Managed Kubernetes Service (AKS) to implement a multi-region PingDirectory cluster using Ping Identity’s official repositories. The implementation can be divided into the following major components:
- Azure AKS
- PingIdentity Server Profiles
- PingIdentity Helm Charts
- PingDataSync Server
Azure AKS:
The node autoscaling feature of AKS enables automated scaling up or down of cluster nodes based on resource demands. AKS can be accessed via the AKS management portal, AKS CLI, or tools like Azure Resource Manager. AKS also supports Continuous Integration / Continuous Delivery (CI/CD) pipelines. We start the implementation by creating two Virtual Networks in two different Azure regions. Azure AKS clusters are then created in subnets within each Virtual Network. Azure CNI as the networking interface to obtain IP addresses from the subnet that the AKS cluster is deployed in. Two-way peering is enabled between the two Virtual Networks.
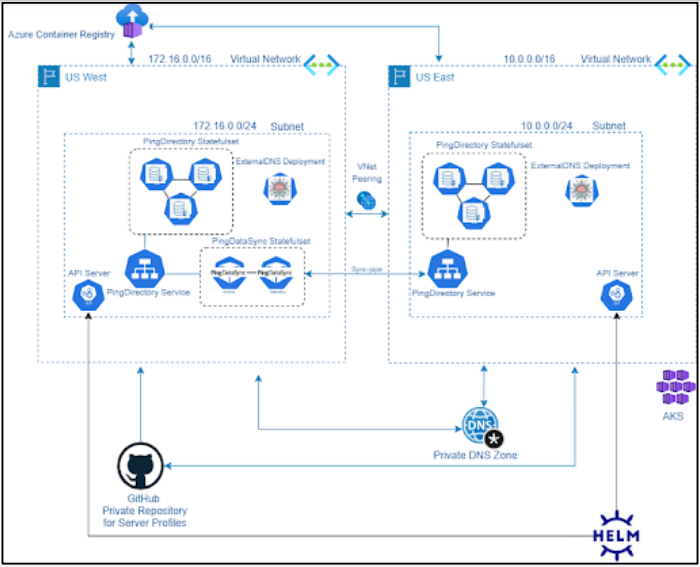
PingDataSync Server:
PingDataSync is a Java-based server that provides real-time or scheduled, bi-directional data synchronization across diverse data sources. PingDataSync Server does not store any data from the endpoints, reducing hardware and administration costs. In this scenario, we will be implementing a real-time, bi-directional sync pipe between PingDirectory Instances in the two AKS clusters.
When compared to enabling cross-cluster replication, using a PingDataSync bi-directional sync pipe for cross-cluster data synchronization eliminates the secondary cluster’s reliance on the seed cluster for dsreplication state retrieval and initialization while allowing for pod auto-scaling of the PingDirectory statefulset in the secondary cluster in the event of unexpected downtime/failure of the seed cluster.
Multi-region Deployment
With the PingDirectory and PingDataSync containers deployed using Helm Charts on Azure AKS, we can now configure the multi-region setup. In this setup, we can configure PingDirectory clusters in different Azure regions using the Azure Virtual Network peering. Each region can have its own PingDirectory cluster with multiple replicas for high availability, and the clusters can be configured for data synchronization using PingDataSync.
We configure the PingDataSync servers to synchronize data between the PingDirectory clusters in different regions. This can be done using the PingDataSync configuration settings, which specify the source and target directories for synchronization. The synchronization process can be scheduled to run in real-time, at regular intervals or upon triggers by specific events.
Benefits of Cloud-First IAM Deployment
The shift toward a Cloud-First IAM deployment strategy offers several benefits for organizations:
Scalability:
Cloud IAM solution deployments can easily scale up or down based on the organization’s needs. With managed cloud services like AKS, organizations can automatically scale the resources based on the load and ensure the high availability of IAM services to meet the demand of the growing user base.
Cost-effective:
Cloud-based IAM solutions and deployments can significantly reduce the cost of infrastructure maintenance, operational overhead, and hardware procurement. Managed cloud services like AKS provide cost-effective options for running IAM services. As organizations only pay for the resources they use, they can easily scale up or down as needed.
Agility:
Cloud-based IAM deployments enable organizations to stay agile and responsive to changing business needs. With containerization and DevOps practices, organizations can quickly deploy and update IAM services, automate testing, and release new features to end-users faster, giving them a competitive edge in the market.
Security: Cloud-based IAM deployments offer robust security features, including identity management solutions, access management, authentication, authorization, encryption, and monitoring. Cloud providers like Azure, AWS, and Google Cloud have strict security protocols in place to protect customer data and ensure compliance with industry standards and regulations.
Challenges and Considerations
While the Cloud-First IAM deployment strategy offers several benefits, organizations should also consider and address some challenges and considerations:
Security and Compliance:
While cloud providers offer robust security features such as identity management as a service in cloud computing, organizations should ensure that their IAM deployments comply with industry standards and regulations and they have proper controls in place to protect sensitive data. This includes managing access controls, encrypting data at rest and in transit, monitoring for security events, and conducting regular security audits.
Integration with Existing Systems: Organizations may have existing IAM systems or other applications that need to be integrated with the Cloud-First IAM deployment. Ensuring seamless integration and data synchronization between different IAM systems or applications may require additional development and customization efforts.
Vendor Lock-In: Deploying customer identity management solutions in the cloud may create dependency on a specific cloud provider and their services. Organizations need to consider the implications of vendor lock-in and have strategies in place to mitigate risks, such as using cloud-agnostic IAM solutions or implementing multi-cloud strategies.
Data Privacy: Organizations need to carefully consider data privacy concerns, especially when dealing with personally identifiable information (PII) or other sensitive data. Data residency and data sovereignty regulations may require specific measures to be in place to ensure compliance, such as data encryption and data access controls.
Operational Management: Managing IAM deployments in the cloud requires proper operational management practices, including monitoring, logging, backup and recovery, and patch management. Organizations need to ensure that they have the necessary tools and processes in place to effectively manage their IAM deployments and ensure high availability and reliability
Conclusion
This blog provides a brief overview of the implementation of a multi-region PingDirectory cluster on AKS to give a better understanding of the components in play and serves as a baseline that can be customized based on the organization’s needs. Like Minds, as a leading provider of cloud-based IAM solutions, can help organizations to overcome challenges such as security, compliance, integration, data privacy, performance, and operational management. With expertise in these areas, Like Minds provides organizations with the tools and resources for a successful IAM deployment in the cloud. Partnering with Like Minds enables organizations to confidently embrace Cloud-First IAM and unlock the benefits of scalability, flexibility, cost-effectiveness, and agility in managing identities and access in today’s digital landscape. Please contact us if you are interested in discussing your organization’s migration from On-Premise infrastructure to the Cloud for Ping Identity’s suite of products. We also offer IAM professional services, IAM consulting, as well as pingfederate developer training