Thani Anandan
Director IDM & Security
How many times would you have wondered if there is an easier way than scurrying for your office laptop, search your key fob and then connect to the VPN to just enter your timesheet?
Is there a route which offers the same level of protection to my data but with a simplified user experience? We are progressing into an age where everything is applications. Access to data, files and folders are presented to the users as an application. When data and resource are available now in a more structured and simplified format, why not the access to data in your enterprise be the same way? These lingering questions led me to research and welcome the new kid on the security block – Identity Aware Proxies (IAP).

Perimeter Security – What are we missing?
Most Enterprises extend security to their workforce by building and enabling a strong outer wall, courtesy of firewalls, VPNs and other appliances. These technologies have been around for quite some time now and it is time for a rethink. Firewalls and VPN technologies which commonly form an Enterprise’s security ring are quite mature and reliable. Once a user is connected to a VPN, they are able to access services, applications and resources that reside within the network. But the problem is that once an attacker is able to breach the walls of your fortress, he is free to roam and wreak havoc on the inside. Moreover, the traditional security model assumes all the users with the VPN are inherently trusted ones. Are there controls on the data, resources that are available inside the network as we had provided on the outer security? Why do I need to get access to the entire enterprise for entering a simple timesheet? I also have to log in multiple times to access resources even after authentication at the perimeter, which leads to a very cumbersome user experience. I also need to be careful about connecting through a public Wi-Fi sitting at a cafe, as I have to be wary of not exposing my enterprise assets just for entering my timesheet!! Yes, that’s what we have in today’s enterprises – a strong outer wall and a vulnerable interior with unstructured controls. How do we solve this? Let’s take a look at the Zero Trust Security Model first before diving into Identity Aware Proxies (IAP).
What is Zero Trust?
Zero Trust Security model eliminates the archaic castle wall security mentality and paves the way towards providing a dedicated micro security perimeter for each application This model never trusts anyone automatically, be it fulltime employees, admins or privileged accounts. Only if the user is able to authenticate, is able to show that he/she has the right permissions to access the resource, verified device profile, etc. would the user be able to gain access to the resource and that too only to the resource and not the entire organization resources. Zero Trust is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access. The Zero Trust Security Model was created in 2010 by John Kindervag. It revolves around the principle to never trust and always verify.
Identity Aware Proxy (IAP)
Identity Aware Proxies are components to implement and enable the Zero Trust Security model. Identity Aware Proxy architecture provide access to application via a cloud based proxy. IAPs intercept the incoming request for an application or an API, authenticate the users, check for policies, authorize the user, check device profile, etc. All this happens with the request still outside the perimeter of the enterprise and only if the user request fully satisfies all the conditions set by the IAP, it is allowed to proceed and the user would be able to access only the application requested for. With the IAP approach, not only are users verified, but the application requests can be terminated, examined, and authorized as well.
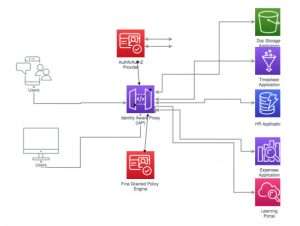
Imagine the user experience, where I as a workforce user can access my enterprise applications on my own device over a public Wi-Fi without the need to implement MDM software on my device or put restricting controls on my device. This is possible with IAP’s implementation of the Zero Trust Model. I would able to enter my timesheet without the fear that I am exposing my enterprise resources over a public Wi-Fi. The timesheet application will have its own private security perimeter provided by the Identity Aware Proxy and only verified and authorized user requests would be allowed to access the application. This is just a simple example. Instead of segmenting your network and dealing with complex network and firewall rules, Identity Aware Proxies can provide secure access to specific applications using a cloud-proxy layer. There is fine-grained access control and authorization. The identity context of the user is evaluated instead of firewall rules allowing the user into the network. IAP can be configured to check for Authentication, Authorization, Multi-Factor Authentication, Time, Location and also device profile attributes. The authentication provider, policy engine/provider can reside outside the network so that the rules engine can apply and monitor policies in real-time before the request actually enters the Enterprise, making changes to access immediately.
Identity Aware Proxy Implementations
The most popular IAP implementation is Google’s implementation of BeyondCorp using Google Cloud IAP. There are other vendors also offering IAP like AWS – Amazon Application load balancer and Microsoft – Azure AD Application Proxy. This is a fledgling concept and many providers like Bitly, ScaleFT are jumping into the fray.
Benefits of Identity Aware Proxies
- They implement the Zero Trust Security Model
- Centralized Policy management specific to identity and applications
- Zero need for endpoint security devices
- Bring Your Own Device (BYOD) is facilitated for the workforce users
- Device profile and device security is evaluated by the IAP.
- Enhanced user experience along with security thereby directly increasing productivity
Can we move forward with IAP?
Identity Aware Proxies provide context aware access to your applications by implementing the Zero Trust Security model without the need for expensive traditional castle wall based security model. The best way to move forward is to start with a hybrid approach wherein your existing security infrastructure is in place and we slowly introduce the ZTM using IAPs for specific applications and then move across to all other applications in the enterprise. Going forward Identity will be the new security perimeter and Identity Aware Proxies would be one of the component to implement this.
About the author
Thani Anandan is a Director – IdM & Security at LikeMinds Consulting Inc. and works on enterprise implementations of IAM and Cloud Security models.